Project Name: Kasagpan Web & Mobile App
Project Team: T04
Start Date: Jan 23, 2017 to Feb 12, 2017
Overall Project Health: 
SUMMARY
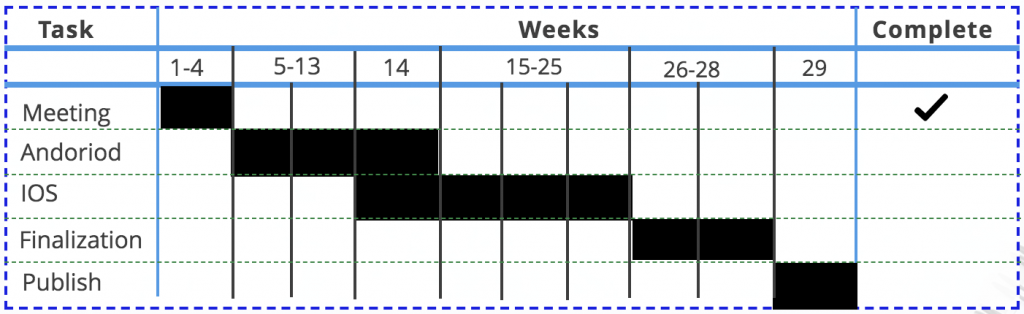
Making sure we have all our pages for the Android application working correctly and applying the code to link the pages with one another are tasks that specifically needs attention because it is a crucial step in order for the app to properly function and to continue onto next tasks. Although we face some risk because we are seen as beginners in mobile development, we still have the confidence that we will have this completed on time. This task may take up most of our time during the Android development process, because we want to accomplish this very diligently, in order to reduce the risk of facing any problems later in the project.
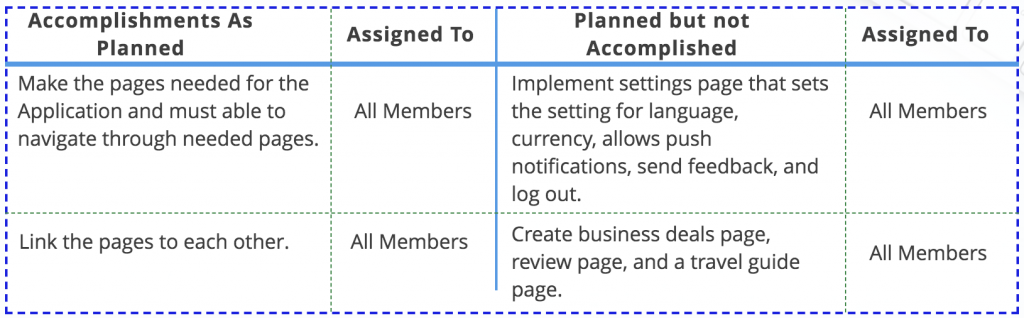
UPCOMING OBJECTIVES
In the next two weeks, we are expecting to have all pages of our Android application fully functional. We will have also completed making all of the necessary pages for the Android mobile application and assembling the pages so that all are linked to each other. We will make sure that the pages have a similar look, in order for guests to easily recognize that they are still using the same application when navigating through pages. The completion of this will greatly reduce our workload and assist us in finishing our project on time. Getting this task done on time will significantly reduce any risk of late completion, also it will give us more time to make the perfect product for our stakeholder.
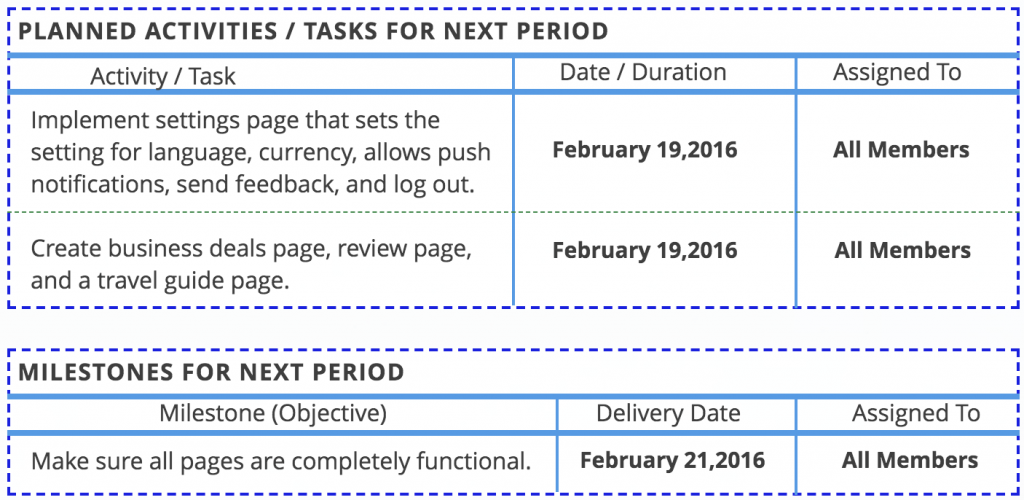
MANAGING ISSUES AND RISK
An item that specifically needs attention is storing client data. Storing this data there can be a potential risk of losing client data such as their password. In order to avoid this, we will be putting the data into a secure repository. To make sure we have a secure application we will be taking some security measures such as making sure the user makes a strong password for their account, making sure we use a secure connection for online payments, and by having backup copies of the data. We may also use a layered security approach and implement some system alerts to detect any suspicious activities.